Enterprise SSO
How to enable SSO (e.g Okta) authentication to OneSchema for your organization
Please contact your OneSchema representative for more info on enabling SSO for your organization.
OneSchema supports single-sign-on (SSO) and Security Assertion Markup Language (SAML) authentication to manage authentication and access to the OneSchema dashboard.

When you set up a SAML authentication method, only users in your organization's identity provider will be able to log into to the application. By default, all other authentication methods will be disabled.
All SAML SSO configurations support "Just In Time" (JIT) provisioning, which allows OneSchema to create users when they log in for the first time.
We support several identity providers including Okta, Microsoft, and Google.
Configuring Okta SAML / SSO
- From the Okta Admin Dashboard, click Create App Integration in the Applications tab
- Select SAML 2.0 and continue to the the General Settings form, enter the name of your application as OneSchema.
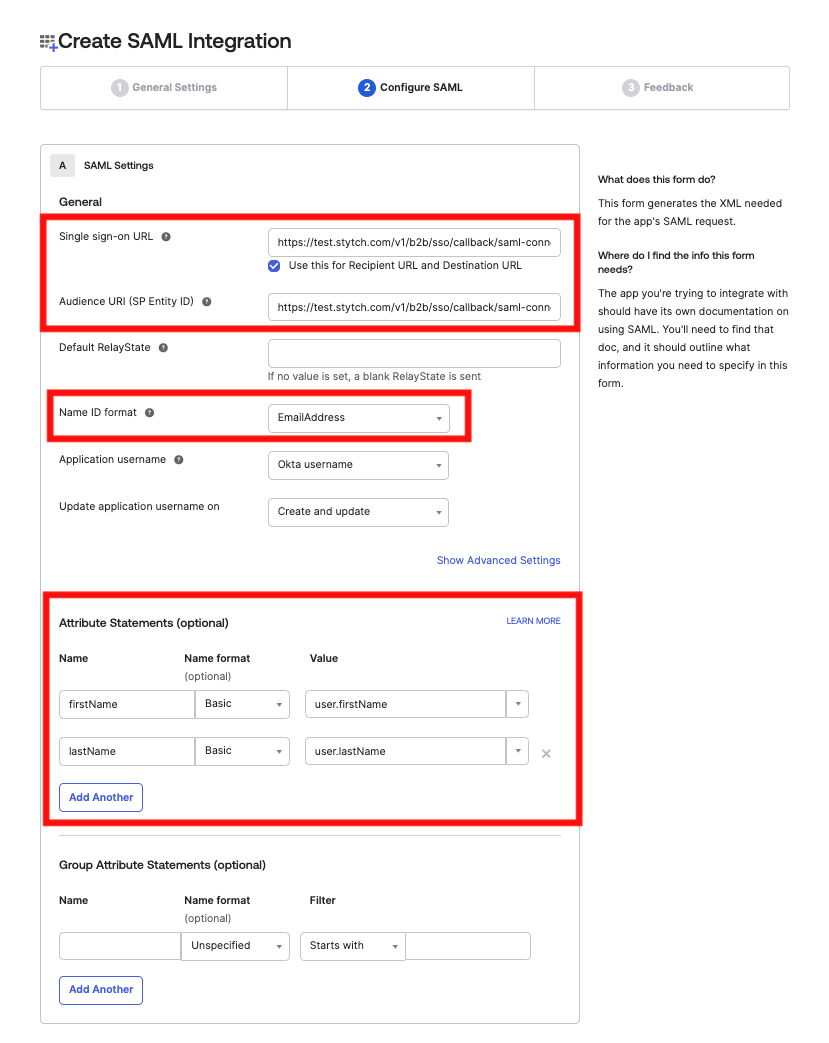
- In the Configure SAML form:
- Input the
acs_urlas the Single sign-on URL. This will be provided by your OneSchema representative. - Input the
audience_urias the Audience URI (SP Entity ID). This will be provided by your OneSchema representative. - Select EmailAddress for Name ID format
- In Attribute Statements create two inputs:
Name: firstName; Name format: Basic; Value: user.firstName
Name: lastName; Name format: Basic; Value: user.lastName
- Input the
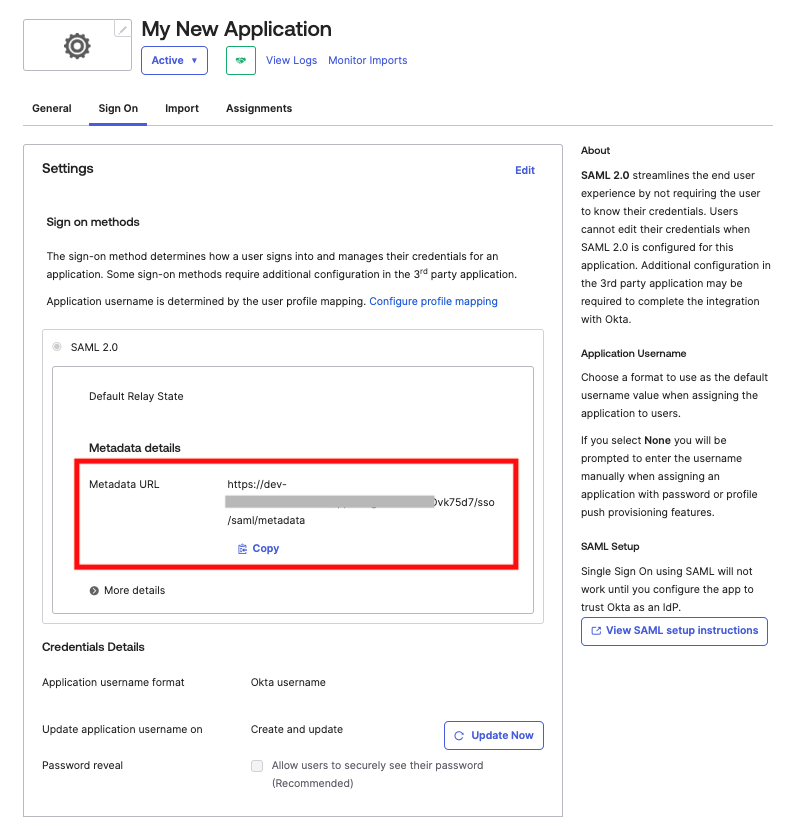
- Save and continue, indicating that this is an internal application on the last screen. Copy the Metadata URL from the Sign On Settings tab in your newly created Okta application and share this with your OneSchema representative.
Updated 5 months ago
